Reminder for your Training @ DeepSec 2020: Bypassing CSP via ajax.googleapis.com – Dawid Czagan
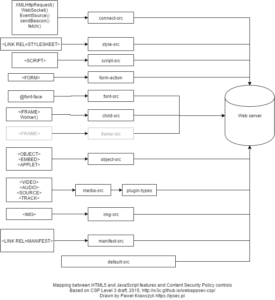 Content Security Policy (CSP) is the number one defensive technology in modern web applications. A good CSP offers a lot of possibilities, but it is hard to develop. Mistakes are common, too. Many developers add ajax.googleapis.com to CSP definitions, because they use libraries from this very popular content distributions network (CDN) in their web applications. The problem is that it completely bypasses the CSP and obviously you don’t want that to happen. Since CSP should be part of any modern application, you better get to work and brush up your knowledge.
Content Security Policy (CSP) is the number one defensive technology in modern web applications. A good CSP offers a lot of possibilities, but it is hard to develop. Mistakes are common, too. Many developers add ajax.googleapis.com to CSP definitions, because they use libraries from this very popular content distributions network (CDN) in their web applications. The problem is that it completely bypasses the CSP and obviously you don’t want that to happen. Since CSP should be part of any modern application, you better get to work and brush up your knowledge.
In a free video Dawid Czagan (DeepSec Instructor) will show you step-by-step how your CSP can be bypassed by hackers.
Watch this free video and feel the taste of Dawid Czagan’s Live Online Training ”Black Belt Pentesting / Bug Hunting Millionaire: Mastering Web Attacks with Full-Stack Exploitation” (training at DeepSec 2020; 17/18 November)
