Surveillance Article: Listening Posts for Wireless Communication
Modern ways of communication and methods to obtain the transported data have raised eyebrows and interest in the past years. Information security specialists are used to digitally dig into the networked world. Once you take a look at buildings, geographic topology, and photographs of structures your world view expands. Coupled with the knowledge of ham radio operators connecting the dots can give you some new information about structures hiding in plain sight. This is why we have translated an article by Erich Moechel, Austrian journalist who is writing blog articles for the FM4 radio station.
Read this article for yourself and keep our Call for Papers for DeepSec 2015 in mind. If you have ideas how to keep an eye on the environment surrounding your information technology infrastructure let us know. Companies should know their neighbours too, don’t you think?
The Surveillance Network over the Rooftops of Vienna
By Erich Moechel, original source fm4.orf.at. Published 17 May 2015.
The roof structures on the US and Britain embassies are nodes of a network for mobile surveillance, which covers large parts of Vienna.
The four hitherto known monitoring stations on these viennese roofs are not isolated “listening posts” (This refers to previous articles describing structures on the roofs of buildings in Vienna, written by the author).

Image showing the structures on the roof. The new panel is made of a different material than the original, grey envelope. The renovation was carried out in spring 2014.
These small sheds sitting on top of embassies and field offices are the four nodes of a network for mobile surveillance, which covers large parts of Vienna. This network is much longer in operation than one might assume. 2014 the camouflage covering the station on top of the US embassy has been completely renovated, two other stations show significant signs of weathering.
As topographical measurements have revealed there is a very good line of sight between the three known US stations. Broadband radio links are easy to implement with small satellite dishes, while the British station further below can only be reached from the IZD Tower located in Vienna 22nd district. This fits in with a key document of the “Special Collectіon Service” (SCS), a joint venture between the NSA and CIA, outlining a monitoring concept for mobile phone networks in metropolitan areas around the world, describing it as an autonomous radio network with its own data processing on site.
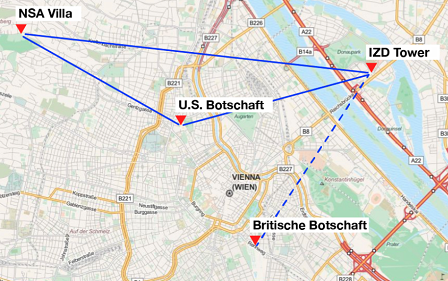
The connection from IZD the British Embassy is shown in dashed lines since it runs only one to two meters above the roof edge. We assume that there is at least one other station that has a clear view on the British Embassy and on another point of the network.
How the Network works
Such a monitoring network collects the key settings of radio cells, their control stations and other important parameters of the three mobile networks of Austria. This data forms the basis for attacks on selected devices, whereby the monitoring of mobile networks on site follows the pattern of fibre optic monitoring. In both cases, the captured metadata gets continually compared with lists of “selectors” or “identifiers”, in mobile networks mainly the IMSI and IMEI numbers of the SIM card or the mobile device.
The British station in 1030 13 Jauresgasse and the station on the IZD Tower show clearly visible signs of weathering and share the same characteristics as the US stations.
As soon as a mobile phone flagged by a selector list logs in to such a monitored radio cell, an alarm goes off automatically as well the following monitoring steps described in the key document of SCS. This automated analysis is mentioned as a core feature of the system. In Vienna this must have been in use since at least 2007.
Appropriate Acronyms, Panoramic Views
The slides that describe the SCS system so clearly are from a conference called SIGDEV, but the title slide refers to internal training documents of the NSA back from 2007, which were re-worked for the SIGDEV Conference 2011. “Signal Developers” are departments of the intelligence services which are responsible for the development of new data sources. This also explains the relatively simple interpretability of this document. It aims to describe the operation system developed by the NSA and GCHQ not to insiders, but to the staff of partner services.
References to the name of this system however, can be found not in this document but in an undated, most likely later document from the Snowden document pool. Only in the glossary contained in a far more extensive document an appropriate acronym has been found: “Stateroom” seems fairly well chosen, referring to the “state room” – cabins on cruise ships, which offer a panoramic view. In addition, these small houses on top of the embassies of the US and Britain are considered to be part of their own territory, as they are placed exclusively on buildings with diplomatic status. Embassies are not extraterritorial by law, but have a similar de facto status, due to diplomatic immunity. …
The SCS “Show House”
The system has become sophisticated: from the “maintenance house” to the wide-band antenna systems, its features are now standardized and can be found in the capitals around the world. Since they form a network, the individual components must be coordinated through the use of standardized, programmable antenna systems, thus the same system can be used on any cellular network in the world. “SCS Modernization” is the title of one of the slides. Another lists the new stateroom features: “modern IT services and infrastructure to support a network-centric model work, improving safety and maintenance”. The latter was achieved by standardizing the equipment.
Standardization not only simplifies the logistics – the technical support is centralized – but also the training of the operating personnel. In the European headquarters of the SCS in Wiesbaden, where they currently build a “Consolidated Intelligence Centre”, even a “show house” for training purposes has been set up. By now we even know its exact size: with 20 square meters, its slightly larger than initially estimated.
Tapped Controller
A whole battery of small satellite dishes can be set up in one of these sheds. Primarily the system is not going after individual radio cells but their control stations. Base Station Controllers (GSM) or Radio Network Controllers (UMTS) in the urban area are typically in charge of more than a hundred radio cells; the whole net ѕegment is called “Location Area” and has the same function as a “Routing Area” on the Internet.
These control stations are permanently collecting metadata from all radio cells, listing location data, IMSI, last known radio cell, etc. of all phones, located in any cell in their respective “Location Area”. The list updates itself constantly because the terminals are mobile, hence, in motion. This generates significant amounts of data that must be processed.
Microwaves
These data are continuously captured by the stateroom stations and transported through the network to a central station for processing. Since stateroom works close to real time, the data in all probability gets transported via radio links, because the so called “Einstein / Castanet” antenna system of SCS is also capable of using these. Furthermore any radio equipment can be connected, including equipment for “Microwave”, in this case not meaning microwave ovens, but radio links around 2 GHz. Since the Einstein / Castanet antenna system is also suitable for transmission, microwave radio links can be built with the same universal antennae between two locations, visual contact is naturally a prerequisite here. Likewise, radio links of mobile operators can be tapped as well.
Most likely the evaluation of the collected data takes place at the NSA Villa, because usually military analysts are working locally on site. The villa in Pötzleinsdorf is a well-nigh prototypical location for such an evaluation point, whereas the IZD Tower in Vienna 22nd district, where the US representative of the United Nations officially resides, is the most likely location for the majority of the technical processing of the data intercepted by the staterooms.
Because some companies moved out, several floors directly below the US mission are vacant. In addition extensions and conversions are taking place, as several sources report unanimously. Here, too, an upgrade took place. In December 2013, after 12 years of operation, the central air-conditioning in the building has been replaced by using a cargo helicopter. The new cooling system, equipped with a cooling capacity of 4.2 MW, is by one third more efficient than the previous model. The need for cooling capacity in the IZD Tower must have risen considerably over the last few years.
Where the Data ends up
Not only the local surveillance networks operate autonomously, the entire system also has its own headquarters near Beltsville, Maryland. At the headquarters of SCS topographies of mobile networks from the capitals of the world are systematically collected and regularly updated. This data is not only only available to the staff of NSA and CIA for attack purposes, but also to the intelligence services of the US Armed Forces and all other “agencies” of the US intelligence complex.
Regarding the SCS network in Vienna, the graph above only shows its backbone and even that not completely, because at least one station, in good visual contact with the British Embassy as well as at least one of the other three known nodes, is missing. Like all military networks this monitoring network acts according to the rules of the “network-centric warfare”, the official US military doctrine since the mid-90s.
