Translated Article: German Cyber Security Strategy without Security
Deutsche Cybersicherheitsstrategie ohne Sicherheit by Erich Moechel for fm4.ORF.at
The new German Interior Minister Nancy Faeser (SPD) is continuing the cyber course of her predecessor Horst Seehofer (CDU), which according to independent experts has been completely misguided. The professional world “is not amused”.
Parallel to the finalization of the new EU directive on cyber security (NIS2), Germany’s new cyber security strategy was presented in Berlin. The European directive, which was negotiated unusually quickly, was welcomed almost unanimously by experts.
The new German cyber security strategy, on the other hand, has been consistently criticized by experts since its publication. As a closer look shows, it is neither new nor a security strategy. First and foremost, new powers are being distributed to police authorities and secret services.
Trojans instead of cyber security
As the table of contents already shows, the primary aim here is not to significantly increase the general level of security in the information networks, as is the case with NIS2. The first four sections, i.e. the top priorities of this approach, concern the German authorities alone. For example, the top priority is to expand the “detection and analysis capabilities” in order to reduce the “dependence of the security authorities on non-European manufacturers”. “Police and intelligence services” would “benefit equally from the expansion of their own national development capabilities”.
The entire second section is dedicated to the expansion of the Federal Office for the Protection of the Constitution and the “Central Office for Information Technology in the Security Sector” (ZITiS), commonly known as the “Trojan Authority”. These national “development capabilities” are intended to “establish effective vulnerability management”. Translated, this means: ZITіS is supposed to supply its own surveillance tools and, above all, Trojan malware for police and secret services in order to reduce their dependence on disreputable companies such as the NSO Group or Candiru (Israel) and US companies. “Vulnerability management” is a procedure in which newly discovered security gaps are first presented to the secret services, which then decide whether these gaps may be made public or whether they are reserved for “personal needs”. That is the exact opposite of the recommendations of almost all independent IT security experts, not only in Germany.
Encryption for government only
In the uppermost points reserved for the authorities, concrete projects are primarily dealt with that have been taken over by the previous conservative government and continued straight ahead. ZITiS is to receive a legal basis and be expanded to become the “central service provider for the security authorities”, especially since “the police and intelligence services would benefit equally from the expansion of their own national development capabilities” and a “central bundling of investments and development capabilities”. In addition, the Federal Office for the Protection of the Constitution is to be expanded to become a “central office function in the Association for the Protection of the Constitution”.
So far so specific. From the point five “Strengthening cyber resilience of critical infrastructures” the tone changes noticeably. Then there is talk of “promotion of investments in cyber resilience measures” and of “awareness and cyber resilience projects” under “consideration of the security of IT supply chains”. Throughout the following four chapters, not a single measure to strengthen this cyber resilience is even mentioned. Encryption occurs only twice in the entire document. In the first case as an obstacle for prosecutors and then to “equip the federal authorities with advanced IT products”, namely “quantum computing and post-quantum cryptography”.
Preliminary conclusion
The final chapter “Create crisis-proof communication capability and expand network security” also only affects the authorities, but not the critical infrastructure itself. Here, only the public service is mentioned and, once again, there’s a rant about “national digital sovereignty”, which is threatened by “cyber attacks by foreign powers”. “Such geopolitical power fantasies – regardless of whether internally or externally – no longer belong in security concepts in the 21st century,” said Manuel Atug, an expert in IT and cyber security at AG Kritis to ORF.at “Security needs to be thought through and human protection must be thought of from the point of view of the individual”, which is not the case in this case.
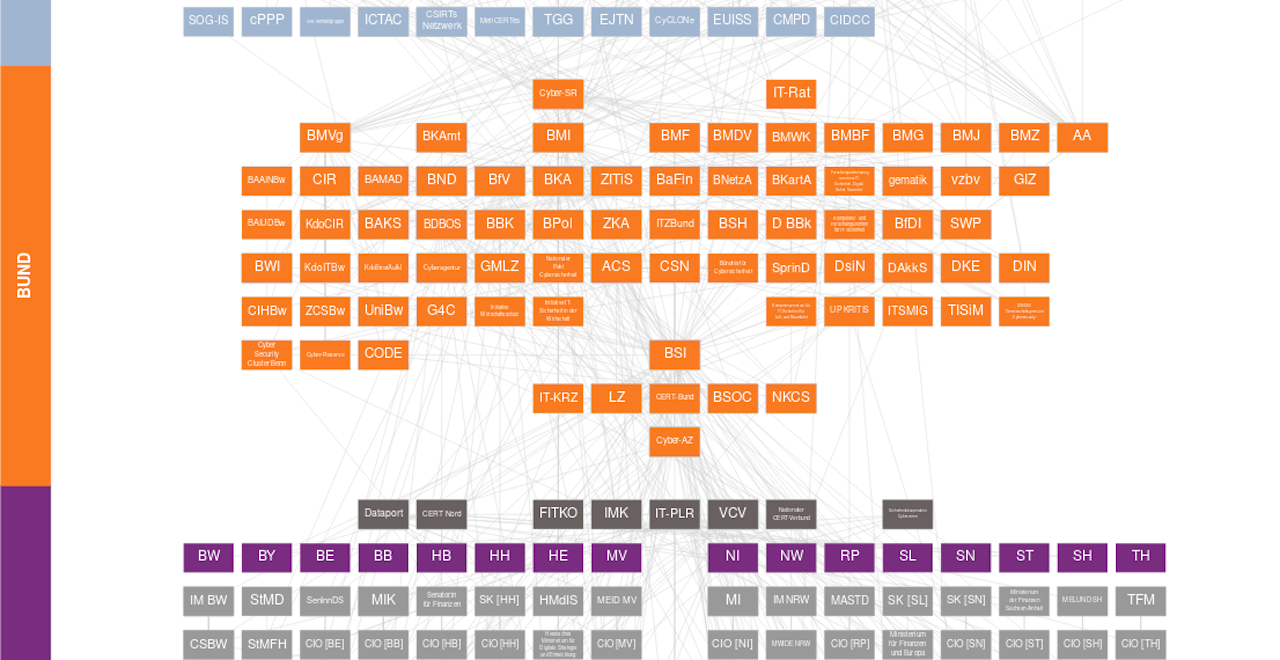
This is an excerpt from the (unofficial) organization chart of German cyber security, compiled by the Stiftung New Responsibility. The diagram shows the public bodies that are activated in the event of a cyber attack. The top row (grey-blue) are EU organisations, below them the bodies and institutions of the German Federal Government are shown in orange. The lowest institutions shown here show the country levels, whereby this screenshot only shows an excerpt of less than half of the entire organizational chart.
Epilogue
The organization chart above continues endlessly downwards, namely to where, for example, ransomware attacks actually “impact” in the area of critical infrastructure. This happens primarily with municipal service providers of all kinds, regional administrative authorities, smaller hospitals, SMEs and similar units that are at the bottom of the hierarchy. How, in such a bloated bureaucratic construct, absolutely time-critical decisions should be made and countermeasures initiated in near real time, those responsible probably don’t know exactly themselves.
Perhaps all of this is on purpose, however, in order to irritate potential cyber attackers with this bureaucratic overkill so much that they lose sight of their actual attack targets.
